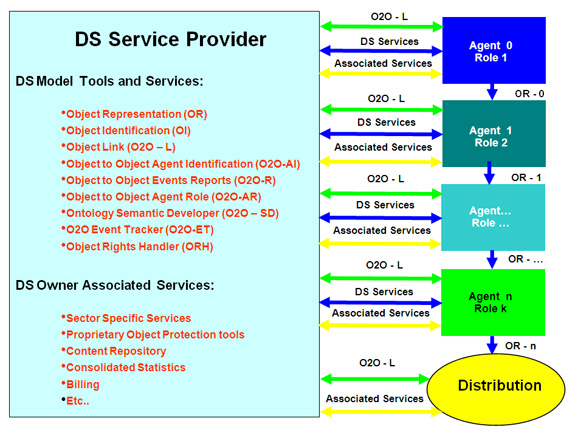
Introduction NPI’s base product is a suite of tools for application development generically denominated “Digital Shadow Caster tm” (DSC). DSC allows for the digital representation of objects (concrete or abstract) in applications called Digital Shadows (DS) that link objects through the events and actions taken on the objects. The management of the resulting network of object/events/actions relationships becomes a powerful tool for commercial and non commercial product management of the real objects being represented. Furthermore, the greatly reduced cost of operating a DS on behalf of communities of users makes this technology practically available to any entity, organization or individual. Thus, the life cycle of any real object may “Cast” a “Digital Shadow” (DS) that allows the related communities to capture and share real time key information, events and actions. Each DS allows for the ordered delivery of proprietary services managed over a predictable and transparent network of Object Representations (OR) in Object to Object (O2O) relationships determined by the Actions and Events performed on the objects by agents with pre-determined (trusted) Roles. The main building blocks of Digital Shadow Caster applications can be depicted as follows:
Use Case examples All objects of value from personal documents, collectors’ items, commercial products, produce, yachts, prize animals etc. can be represented within one or more Digital Shadows. Thus throughout any object’s history and according to its owners wishes, all key information, actions and events throughout its life cycle can be made available to the appropriate DS using standard protocols and devices available to all users. In this way, when an object is identified anywhere, either by its intrinsic properties or any other identifier, its Digital Shadow can be consulted for multiple purposes such as sales management, product security and consumer protection. For example:Security and Pedigree of Valuables A world class luthier represents each of the instruments that he builds using a Shadow Caster Application Service and as a protection measure links her/his guaranty, maintenance and authentication of origin policy to the coherence of the objects DS when it changes ownership for example. Such that if the identity of a new owner doesn’t correspond to that recorded in the digital shadow by the previous owner, the object is no longer recognised by its originator removing much of the value of the instrument as a commodity as it nbecomes clear that it may not have been obtained legitimately.Value Network Synergies Members of an Olive Growers’ Guild may Represent their production using a Shadow Caster application such that all products derived further down the value network are given a certified pedigree reflected in the corresponding Digital Shadow. This is a valuable means for identifying the origin of produce and commodities and if introduced as a standard within the Olive Growers’ Guild, would then become the basis for the rest of the network implementing the system. Note that any point of the value network that severs the DS link, would make subsequent products deliberate orphans, losing the benefit of synergy with previous value. On the other hand, maintaining the link would enhance the commercial value of that link making its products more attractive to subsequent links in the network. Also, maintaining the value pedigree would provide powerful marketing information to both consumers and producers throughout the network. As an illustration, please consider the following:Would a value chain driven by child labour sweat shops use Shadow Caster? Would a premium quality produce based value chain use Shadow Caster? By answering such questions, it becomes clear that value networks based on inherent quality, value and transparency can benefit enormously by the use of Shadow Caster’s Value Network Representation to cumulatively enhance Value at each link of the Network right through to the end consumer. Furthermore, making the Shadow Caster information network a tool created by all for all, it becomes a means for generating trust for all users by promoting transparent tracking of the nature and origin of products or services in support of greater guarantees of quality, safety and ethical practices for all concerned. |
||